把数条5cm长的马铃薯条分别浸在蒸馏水和不同浓度的蔗糖溶液中,每隔一段时间测量马铃薯条的长度。如图显示马铃薯条在不同浓度溶液中长度改变的百分率。下列相关叙述错误的是()
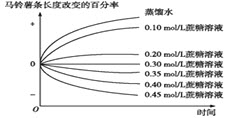
A.马铃薯条通过渗透吸(失)水改变其长度
B.在0.10mol/L蔗糖溶液中马铃薯细胞质壁分离
C.马铃薯细胞细胞液浓度相当于0.30mol/L的蔗糖溶液
D.在0.40mol/L蔗糖溶液中马铃薯细胞失水皱缩
参考答案:B
解析:试题分析:据图分析,马铃薯条浸在0.30M的蔗糖溶液中其长度基本不变,说明马铃薯细胞液浓度相当于0.30M的蔗糖溶液,C正确;浸在低于0.30M的蔗糖溶液中,马铃薯细胞通过渗透作用吸水膨胀,其长度增加,B错误;浸在高于0.30M的蔗糖溶液中,马铃薯细胞通过渗透作用失水皱缩发生质壁分离,其长度缩短,AD正确。考点:本题考查细胞渗透作用的实验,意在考查考生能理解所学知识的要点,把握知识间的内在联系,结合图形分析实验结果的能力。
